Ansible Become
Using Ansible, you can perform various operations on remote machines using Ansible playbooks. By default, an Ansible playbook is executed on the remote host as the same user on the Ansible controller. That means if you want to run a command as another user on the remote machine, you will need to specify it explicitly in the Ansible playbook. Here Ansible become comes into the picture.
To execute the playbook as another user, you will need to provide the sudo feature. The Ansible become directive allows you to run commands as the specified user.
Ansible 'become' is used for privilege escalation. Ansible "become true" is used to activate privilege escalation. Ansible "become user" defines the user which is being used to execute the tasks which has the privileges to run that task.
Let's try to understand this with the help of an example. Consider the below playbook:
- name: this is our first play.
hosts: webserver
tasks:
- name: "create a dummy file on websever1"
lineinfile: dest=/etc/resolv.conf line="gaurav0"
This playbook will write a line "gaurav0" to the file /etc/resolv.conf. Before that we need to check the user of this file, the user and group of the file is root.
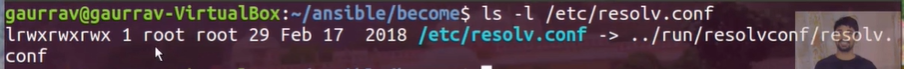
And the user will be, ansible_user=gaurrav
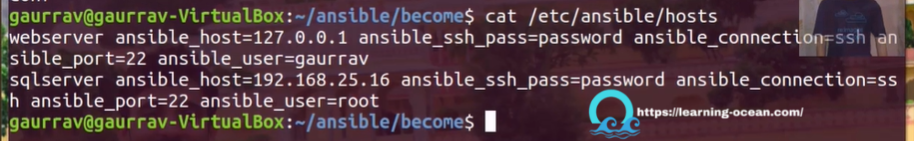 In this case, the user 'gaurrav' should not be able to modify the file as it will be a security threat. Let's try to run the playbook:
In this case, the user 'gaurrav' should not be able to modify the file as it will be a security threat. Let's try to run the playbook:
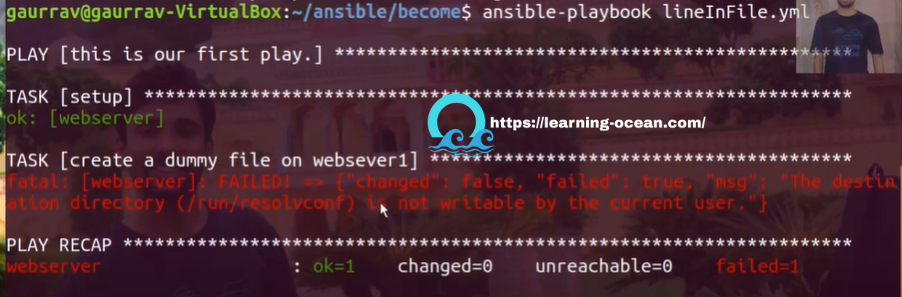 As you can see the error : **"The destination directory is not writable by the current user." **
As you can see the error : **"The destination directory is not writable by the current user." **
To solve this issue, we can run Ansible tasks as a sudo user.
How to Run Ansible Tasks as Sudo
To run an Ansible task as a sudo user, you can use the sudo : yes directive and pass the user's username to execute the task. This is similar to that of using the sudo command in Unix. To achieve this, add below lines in the playbook -
- name: this is our first play.
hosts: webserver
sudo: yes
tasks:
- name: "create a dummy file on websever1"
lineinfile: dest=/etc/resolv.conf line="nameserver 8.8.8.8"
But, for running this playbook, we need to provide the password as well for the sudo privilege. The same can be achieved by passing the ask-become-pass flag in the Ansible command as below -
$ ansible-playbook lineInFile1.yml --ask-become-pass
This command will prompt for a password before executing.
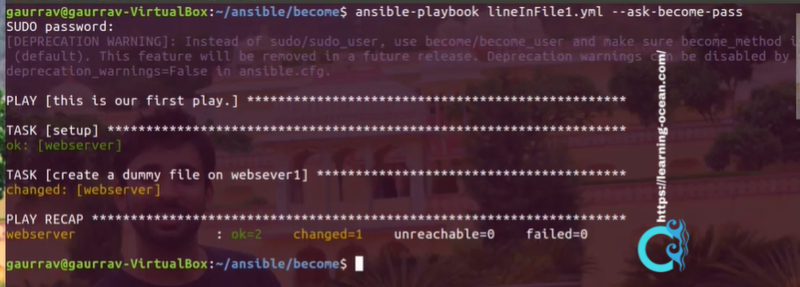
Verifying the /etc/resolv.conf file -
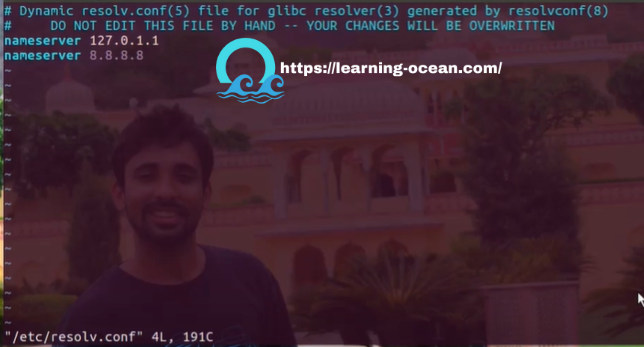
The above task can be achieved as the root user, you can implement the become directive and set the value to 'true' as shown below-
- name: this is our first play.
hosts: webserver
become: true
become_user: root
tasks:
- name: "create a dummy file on websever1"
lineinfile: dest=/etc/resolv.conf line="nameserver 8.8.8.8"
How to Run Ansible Tasks as a user other than root
To run an Ansible task as a specific user, rather than the normal root user, you can use the become_user directive and pass the user's username to execute the task. This is similar to sudo -u command.
Always remember to activate the become directive first by setting become: yes , as the become_user is unusable without this directive activated.
Consider the following playbook, in this the command is executed as the saurav user.
- name: this is our first play.
hosts: webserver
become: yes
become_user: saurav
become_method: su
tasks:
- name: "login username"
command: touch /tmp/become_saurav.txt
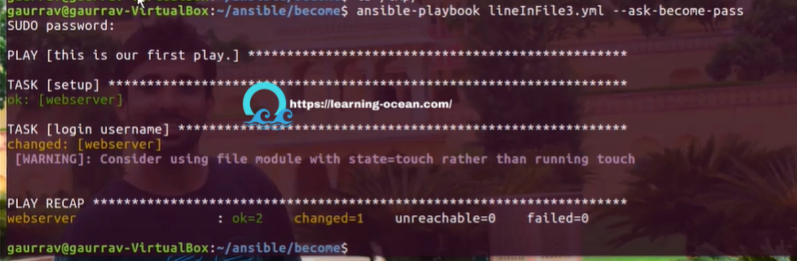
Here, pass the password for 'saurav' user. As a result, a file with the specified name and user 'saurav' would have been created.
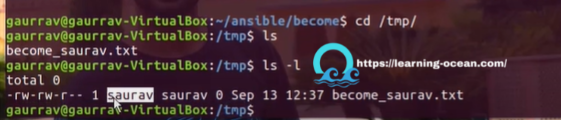 For security reasons, it is better to implement restrictions for various accounts and explicitly specify when they are used. So, privilege escalation is an important aspect of using sudo and su in Ansible.
For security reasons, it is better to implement restrictions for various accounts and explicitly specify when they are used. So, privilege escalation is an important aspect of using sudo and su in Ansible.